Contents
- Introduction
- General Information
- Contact Center Configuration Process
- Initial General Configuration
- Inbound Voice and Chat Service Configuration
- Outbound Campaign Configuration
- Email Service Configuration
- Users and Teams
- Overview
- Users
- Forwarding and Voicemail Operation
- Teams
- Agent Dashboard Metrics
- Roles
- Privileges
- Skill Levels
- Help Screens
- Directory
- Scenario Entries
- Scenarios
- Services and Campaigns
- Services and Campaigns Overview
- Properties Tab
- Assignments Tab
- Lists Tab
- Dispositions Tab
- Activity Tab
- Numbers Tab
- Service Level Tab
- Outbound Tab
- Results Tab
- Archive Tab
- Canned Tab
- Email Tab
- Pre-defined Dispositions
- Outbound - General
- Outbound - Calling Hours
- Outbound - Dial Rules
- Outbound - DNC
- Outbound - Diagnostics
- Activity Forms
- Lists
- Tasks
- Call Center Configuration
- General Settings
- Integration Accounts
- Knowledge Base
- Calendars
- Hours of Operation
- State Calling Hours
- Auxiliary Skills
- Audio Treatments
- Shared Voice Segments
- Voicemail
- Omni-Channel Routing
- Chat Settings
- Email Settings
- Quality Management
- Reporting
- Security
- 1 Security Policy
- Appendices
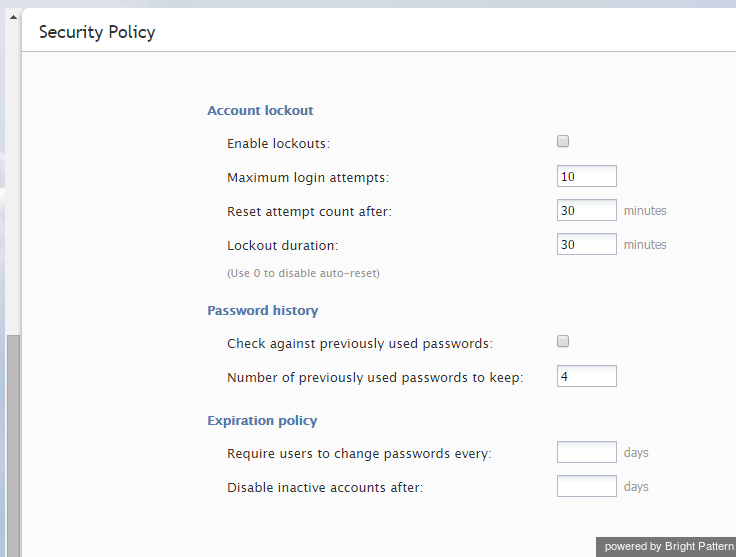
Security Policy
Your system can be configured to automatically lock out a user account after a number of unsuccessful login attempts. An account locked-out in this manner can be subsequently unlocked either manually or automatically after a configured timeout.
You can also configure the system to force your users to change their passwords after a specified number of days, prevent them from submitting previously used passwords, and automatically disable inactive accounts.
Note that your service provider may also impose some password complexity rules, such as minimum password length, mandatory use of various character groups, and exclusion of weak passwords (e.g., usernames). If any such rules are imposed, you cannot change them. You should get description of these rules from your service provider and inform your personnel about them.
To configure security policy settings, select the Security Policy option from the Security menu.
The Security Policy screen properties are described in the following table:
| Security Policy screen properties | |
|---|---|
| Enable lockouts | Indicates whether the account lockout option is enabled.
To comply with the PCI DSS security standard, this option shall be enabled. |
| Maximum login attempts | Number of consecutive unsuccessful login attempts after which the account will be locked out.
To comply with the PCI DSS security standard, set this parameter to at least 6 attempts. |
| Reset attempt count after | The amount of time after which the counter of unsuccessful login attempts will be reset. |
| Lockout duration | The amount of time after which a locked-out account will be unlocked automatically. To disable auto-unlocking set this parameter to “0” – in this case locked-out accounts can only be unlocked manually.
To comply with the PCI DSS security standard, set this parameter to at least 30 minutes. |
| Password history | This section allows you to prevent the user from submitting a new password that is the same as any of the specified number of previous passwords that he used.
To comply with the PCI DSS security standard, select the checkbox and set the number to 4 (or greater). |
| Expiration policy | This section allows you to specify (1) how often users will be required to change their passwords and (2) after how many days inactive user accounts will be disabled.
To comply with the PCI DSS security standard, set both parameters to no more than 90 days. |