Encryption Key Management
Bright Pattern Contact Center supports optional encryption for various data elements that are stored in the system and may contain sensitive information about your customers. This includes voice and screen recordings, chat and SMS transcripts, and email texts and attachments. For more information about enabling encryption for these data elements, see section Encryption. Custom fields of calling lists and activity forms can also be encrypted. For more information, see section Lists of this guide and section Field of the Bright Pattern Contact Center Form Builder Reference Guide, respectively.
The AES-256 algorithm is used for encryption.
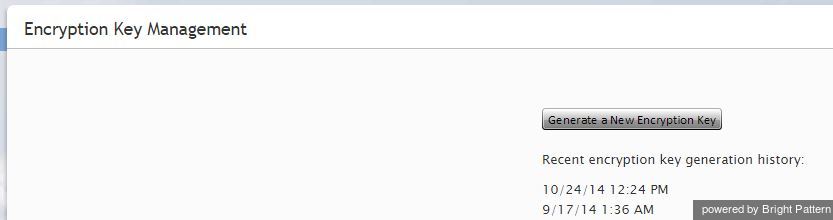
Before you can use the encryption capability, it must be enabled for your contact center at the service-provider level. When this capability is enabled, a data encryption key will be generated automatically by the system. You can manually generate a new encryption key at any time. To generate a new data encryption key, select the Encryption Key Management option from the Security menu and click the Generate a new encryption key button.
Old encryption keys are stored in the system; they are used to decrypt the data that was encrypted using those keys. You can view the date and time of generation of the current and previous keys.
Note that in compliance with various data security standards, data encryption keys themselves are encrypted with a key encryption key (KEK), which is stored separately.
When you export any encrypted items out of the system, they will be unencrypted for export.