Contents
- Introduction
- General Information
- Contact Center Configuration Process
- Initial General Configuration
- Inbound Voice and Chat Service Configuration
- Outbound Campaign Configuration
- Email Service Configuration
- Users and Teams
- Overview
- Users
- Forwarding and Voicemail Operation
- Teams
- Agent Dashboard Metrics
- Roles
- Privileges
- Skill Levels
- Help Screens
- Directory
- Scenario Entries
- Scenarios
- Services and Campaigns
- Services and Campaigns Overview
- Properties Tab
- Assignments Tab
- Lists Tab
- Dispositions Tab
- Activity Tab
- Numbers Tab
- Service Level Tab
- Outbound Tab
- Results Tab
- Archive Tab
- Canned Tab
- Email Tab
- Pre-defined Dispositions
- Outbound - General
- Outbound - Calling Hours
- Outbound - Dial Rules
- Outbound - DNC
- Outbound - Diagnostics
- Forms
- Lists
- Tasks
- Call Center Configuration
- General Settings
- Integration Accounts
- Knowledge Base
- Calendars
- Hours of Operation
- State Calling Hours
- Auxiliary Skills
- Audio Treatments
- Shared Voice Segments
- Voicemail
- Omni-Channel Routing
- Chat Settings
- Email Settings
- Quality Management
- Reporting
- Security
- Security Policy
- 1 System Access Restrictions
- Encryption Key Management
- Text Masking in Chat
- Audit Log
- Appendices
System Access Restrictions
The PCI DSS and some other security standards and regulations require two-factor authentication where, in addition to a password, another method is used to confirm the identity of the user. To support this requirement, the system can be configured for access from a limited number of predefined IP address ranges.
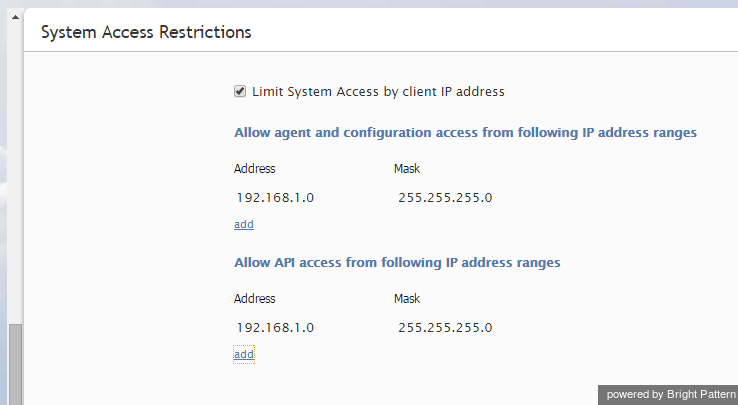
To configure such IP address ranges, select the System Access Restrictions option from the Security menu.
To enable IP address verification, select the Limit system access by client IP address checkbox.
Define the range of IP addresses for the Agent Desktop and Contact Center Administrator applications and, if necessary, for access via APIs.
The desired IP address range should be expressed as a combination of the base IP address and a mask. The mask is used to define which bits in the base IP address are fixed and which bits are variable. A 1 bit is used to indicate a bit in the IP address that is fixed, while a 0 bit indicates that the bit is variable. Use variable bits will form the desired range.
Example Usage
If you set the following, System Access Restrictions will be from address 192.168.64.0 to address 192.168.64.63.
- Address: 192.168.64.63
- Mask: 255.255.255.192
If you set the following, System Access Restrictions will be from address 192.168.64.128 to address 192.168.64.192.
- Address: 192.168.64.128
- Mask: 255.255.255.192