From Bright Pattern Documentation
Encryption
Recordings and transcripts of all your contact center interactions can be encrypted while they are stored in the Bright Pattern Contact Center system.
Before you can use the encryption capability, it must be enabled for your contact center at the service provider level.
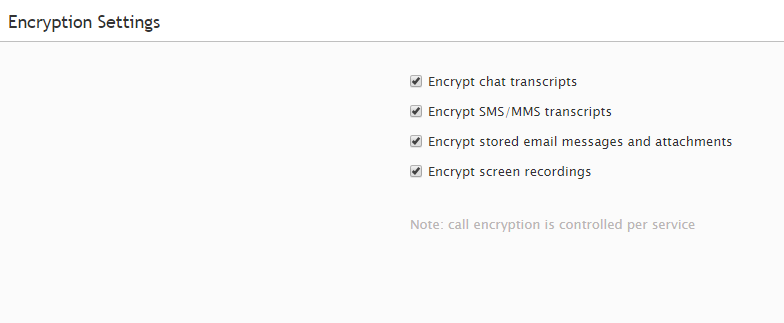
To enable encryption, go to Security > Encryption Settings and check the items that you intend to store encrypted.
Select from the following:
- Encrypt chat transcripts
- Encrypt SMS/MMS transcripts
- Encrypt stored email messages and attachments
- Encrypt screen recordings
Note that encryption of call recordings is configured for each service separately.
When you export any encrypted items out of the system, they will be unencrypted for export.
For more information about the method and keys used for encryption, see section Encryption Key Management.